
Stay updated!
Subscribe to our Newsletter and get notified on latest releases.


Did you know that your WordPress website could be vulnerable to a silent threat known as a replay attack? These stealthy attacks can compromise your site's security, leading to data breaches and unauthorized access.
Did you know that replay attacks have led to massive data breaches and compromised countless websites? If you're running a WordPress site, understanding this threat is critical.
WordPress websites seem to be prime targets for hackers. Replay attacks are a significant threat to website security today. But what exactly are the replay attacks, and are they applicable to WordPress website security?
We will discuss the nature of replay attacks, how they work, and whether they can pose a risk to WordPress security. We will also show ways to protect your website from the attack and other potential vulnerabilities. Let’s move on!
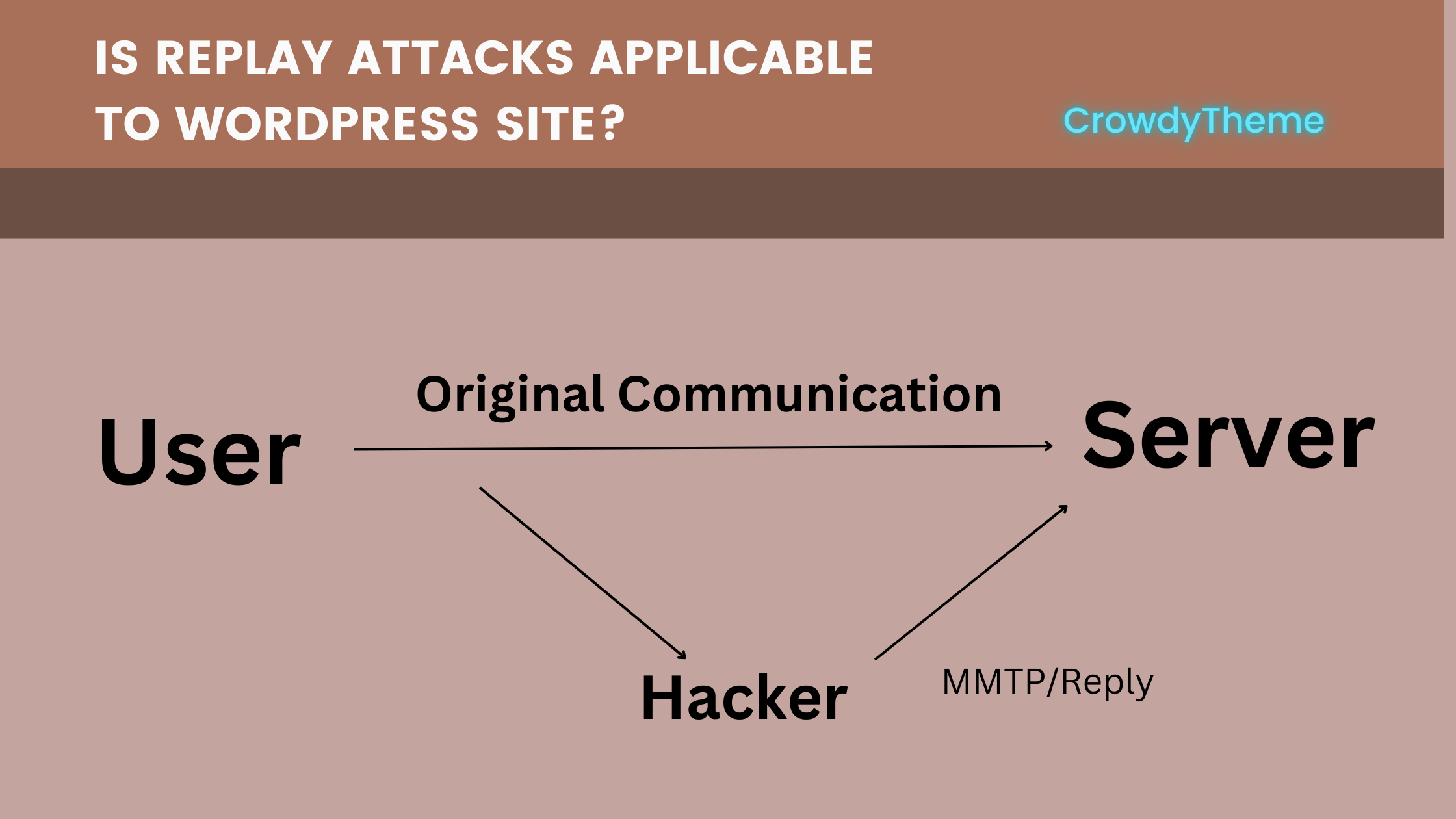
A replay attack occurs when an attacker intercepts and replays valid data to trick a system into accepting it. Once inside, they capture legitimate data such as login credentials or payment information. Then the hacker sends the data to their targeted server and the original receiver.
Replay attacks target systems that fail to verify the freshness of requests or ensure that the same data is not reused. In this case, the attacker replays the intercepted data as if it were an original transmission.
Imagine an attacker captures a user's session token after they log in to a WordPress site. They could then replay this token to impersonate the user and gain unauthorized access to their account.
An attacker might intercept a login request containing a user's username and password. By replaying this request, they could attempt to log in multiple times, potentially bypassing login limits or triggering brute-force attack detection mechanisms.
Here's how hackers attack:
Yes, replay attacks can affect WordPress sites. A recent WordPress plugin vulnerability allowed attackers to intercept and replay API requests, leading to unauthorized data access and potential site compromise.
WordPress offers robust security features, but it is still vulnerable to replay attacks. Especially, when data transmission is not encrypted or properly authenticated.
WordPress sites are at risk when users interact with login forms, submit sensitive data, or make transactions. If the communication between the user and server isn’t encrypted, attackers can potentially intercept and reuse data.
WordPress sites may be less secure than specialized systems like banking platforms if not properly configured. WordPress uses methods or encrypted systems to verify data communication channels and data transmission.
In 2023, a popular e-commerce plugin was found to be vulnerable to replay attacks, allowing attackers to intercept and replay payment requests, resulting in fraudulent transactions.
Here are some of the most common targets:
Login pages are among the most frequent targets of replay attacks. If an attacker captures valid login credentials or session tokens, they can replay the data to gain access to user accounts or administrative panels.
Many WordPress plugins and themes rely on APIs to communicate with other services or the WordPress core. If these API endpoints are not secured with encryption or proper request validation, they can be targeted for replay attacks.
For WordPress-powered eCommerce websites using WooCommerce or similar platforms, replay attacks can be disastrous. If an attacker captures payment data like credit card information or payment tokens, they can replay this data to initiate fraudulent transactions.
Any form submission on a WordPress site that involves sensitive data, such as contact forms or survey submissions, could be a target. If the data is transmitted without proper protection, an attacker might intercept and replay the data to submit false information.
A successful replay attack targeting an admin login can give attackers full access to the website’s backend. For websites that don’t implement strict session management or require additional authentication steps, this is a serious risk.
Luckily, there are several measures you can implement to protect your WordPress site from replay attacks. These steps not only enhance security but also help ensure the integrity of your website’s data transmissions.
The first line of defense against replay attacks is ensuring that all data exchanged between users and the server is encrypted. Enforce HTTPS across your entire WordPress site by installing an SSL certificate. This protects data from being intercepted in transit and makes it far more difficult for attackers to capture sensitive information.
Enable multi-factor authentication (MFA) for users, especially administrators. MFA adds a layer of security by requiring users to verify their identity through something they have or something they are. This reduces the impact of replay attacks, even if login credentials are intercepted.
Nonces are a powerful way to prevent replay attacks in WordPress. By generating unique nonce tokens for each request, WordPress ensures that each action performed on the website is unique. Nonces can be used in forms, API requests, and other critical interactions to verify that the request has not been replayed.
Implementing strong session management is key to preventing replay attacks. Use short session lifetimes and automatically expire sessions after a set period of inactivity. Additionally, make sure that session tokens are rotated frequently and are not reused.
Outdated software is often the source of vulnerabilities. Regularly updating WordPress core, themes, and plugins ensures that any security patches or fixes related to replay attacks are applied. Always check for updates, especially when a security vulnerability is discovered.
Restrict access to sensitive parts of your WordPress site. Use role-based access control to ensure that only authorized users can interact with crucial parts of your website, such as the admin panel or payment systems. Limiting access reduces the potential impact of a replay attack.
Monitoring user activity can help you detect unusual behaviors that may indicate a replay attack or other forms of intrusion. Enable logging to track login attempts, changes to admin accounts, and other critical activities on your WordPress site.
If you run a high-security website or a platform with sensitive transactions, consider using the below-advanced security measures to prevent replay attacks:
Rate Limiting: Implement rate limiting to restrict the number of login attempts or API calls that can be made within a short time frame. This can help prevent automated attacks.
Replay attacks are a genuine threat to WordPress site security, but with proactive measures, you can effectively safeguard your website. Implementing encryption, using nonce tokens, enabling multi-factor authentication, and keeping your WordPress installation and plugins updated are crucial steps in minimizing vulnerabilities.
Remember, website security is not a one-time task—it’s an ongoing process. Regularly audit your site, monitor user activity, and stay informed about emerging threats. By doing so, you can protect your site, secure user data, and maintain trust with your audience.
Take action today to strengthen your website’s defenses and stay ahead of potential attackers!
You might also like
The most critical components of a WordPress site include the theme, plugins, hosting, site structure, and security measures. These elements ensure a smooth, fast, and secure user experience, supporting the site's overall
Do you want to protect your WordPress site with a comprehensive vulnerability scan using VirtualBox? Setting up a virtual machine, installing WordPress, and using advanced tools can help you to identify and resolve potential security threats in a safe testing
Are you concerned about the security of your WordPress admin email addresses? Hackers are constantly evolving their tactics, making it essential for website owners to stay one step ahead. This guide explores how hackers mine WordPress sites for admin emails